-
Posts
4,937 -
Joined
-
Days Won
304
Content Type
Profiles
Forums
Downloads
Gallery
Posts posted by ShaunR
-
-
-
QUOTE (normandinf @ Apr 30 2009, 10:30 PM)
So it must be impossible to do this then

http://lavag.org/old_files/monthly_04_2009/post-15232-1241128886.png' target="_blank">
-
Whats the micro controller expecting?
-
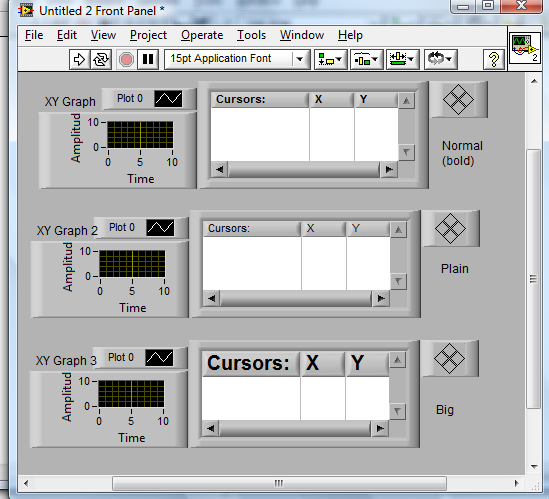
You can change the cursor legend font as with any other indicator/control.
Just set the font of the cursor legend to "Plain". Then they won't be bold.(If that's all you need to acheive).
-
QUOTE (bEMOL @ Apr 30 2009, 12:14 AM)
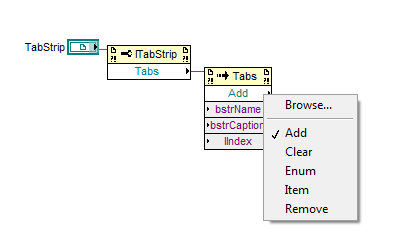
This has the methods to add, delete,clear etc.
http://lavag.org/old_files/monthly_04_2009/post-15232-1241110320.png' target="_blank">
-
There's an example in the Labview examples directory of a tank filling system. Might be worth a look.
-
QUOTE (jdunham @ Apr 30 2009, 02:45 AM)
I'll take a look later...thanks.
QUOTE (jdunham @ Apr 30 2009, 02:45 AM)
That's an interesting quote. I think just shows that the NI VISA team is not on the forefront of LabVIEW development (to be fair, I don't know how old that doc is). Their API could easily accept a VI reference and invoke VI.Run on it when the event happens. They could also accept an occurence or a queue refnum, but I think it would make more sense to do the VI reference. Then inside that VI you could invoke whichever queues or notifiers or occurrences (or polled globals) you need to interact with your running processes. LabVIEW with a callback (which you can also implement in your own code with a private notifier or a VI reference) is no less event-driven than C code with a callback.JasonYou may be right. In fact, there ARE callbacks, in the true definition of callbacks (well in 8.6.x at anyrate). I've been playing with them for my event problem (well its not really a problem, it would just greatly simplify code and maintenance). But VISA doesn't expose the event refnum so you can't attach a callback. Or conversely, callbacks don't accept VISA resource sessions.There is/isn't/probably a way to get at it, but that aspect isn't on my priority list at the mo.
I would go one statment further. Labview is event driven (in the context of truly asynchronous events) with a callback, however C is not event driven....ever.
-
No. Your DAQ definitely won't be enough to drive the motor. Motors are high current devices. You will need a separate power supply and control it via that.
I agree with carlover in so much that really you need a dynamic tracking system (as well as it has been done before).
You will also probably want to go backwards and forwards, as well as up and down (since the sun tracks in an arc and starts in the east and sets in the west every day) so a single motor probably won't be enough (2) and they will need to rotate in both directions.
You might find this useful in thinking about what you want to acheive.
Although I'm at a loss as to why it took 13 weeks...lol.
-
QUOTE (Mark Yedinak @ Apr 29 2009, 09:53 PM)
But the full development license of LabVIEW is NOT required to run a TestStand deployment. Trust me, we are deploying systems here without a full license of either LabVIEW or TestStand installed on the machine. The LabVIEW runtime engine gets installed and a deployment license of TestStand is installed. The only cost for the deployed system is the $500 TestStand deployment license.Read the thread again from 7 posts up.
-
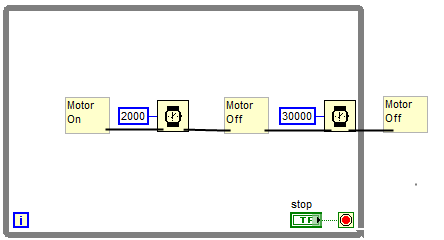
Short answer "yes".
We need to know more too.
How are you interfacing to the motor (is it RS232 , PWM card, digital card, parallel port, force of will?).
Regardless of the interface, you will need a while loop that generates a timed pulse.
It'll look something like this
There are many examples in the Labview examples directory. I would take some time to look at them as quite often you can modify them to suit your needs.
-
QUOTE (Mark Yedinak @ Apr 29 2009, 03:50 PM)
Actually a deployment license is only $500. Granted, you still have a license cost per installation but they do not have to purchase the entire TestStand license. These deployments work essentially the same as a standalone LabVIEW application with the runtime engine.We were talking about a full Labview development environment my comment was aimed at this
QUOTE
TheLVdevelopment environment is very useful in debugging on the fly if you have live code. NI even supports it with a licensing option.Since the OP said he deploys the vi's and anyone can change them (have to have labview on there for that). That is more than $500.
-
QUOTE (shoneill @ Apr 29 2009, 02:03 PM)
If you have registered for an event and the event fires one of the parameters passed at the left-side of the event structure is the actual event refnum. In my mind this does not belong there but you could theoretically close this reference and kill all other processes "listening" to the event in other places.Shane.
Ah. Thats not it then. I'm looking for a way to link events from dynamically loaded vi's So that the vi can basically "hook" the existing event mechanism.
-
-
QUOTE (manojba @ Apr 29 2009, 08:00 AM)
Hi, how to create hypertext link in labview i have splash screen for about button, in the splash screen I have my companys website link as of now its a underlined text how to make it a hyperlink so when somebody clicks on it it should open the website thanks in advance...Hmm. Got me thinking. This would be a good one for a Coding Challenge.
Who could write the best URL Label XControl.
Be nice to be able to just plonk one on the FP.
-
QUOTE (jzoller @ Apr 13 2009, 09:40 PM)
The LV development environment is very useful in debugging on the fly if you have live code. NI even supports it with a licensing option.... yes, I know, everything is always tested before it hits the floor, and no one would ever dream of pig testing so that widget can ship by Friday. Right?
Joe Z. (not my current employer, btw)
I'm thinking more about the cost of deployment. Exes and dll's are don't require licensing.I'd find it impossible to justify that the customer pays thousands for a full package which he/she never uses just so that they can use my software.
-
QUOTE (candidus @ Apr 29 2009, 09:02 AM)
In LV7.1 you can open a VI reference to a VI that resides in a DLL or EXE.Wire its path to the "Open VI Reference" primitive,
the parent "folder" of the VI is the DLL or EXE.
But I think things get complicated if you want to use DLLs/EXEs
built with different LabVIEW versions.
Much better solution.
-
The "Specify path on diagram" is the way forward but I don't think that exists in 7.1 (long time since I used that). So you would have to use the old method of creating an intermediary DLL which you can call from the "Call Library Function node" to pass data too and from other the other DLLs. (2D array in and out always worked best for me). Not elegant, but it works.When you create the plugins, if you make their inputs/outpts are a 2D array then your intermediary dll only needs 2 inputs (the dll name and the 2D array) and one output (2D array).
-
QUOTE (jbrohan @ Apr 27 2009, 02:30 PM)
HelloI have the need to read MMS without going to a cell phone aggregator company. The approach I offer here is not at all an example of good programming practice and it would be much better to gain access to a cell phone company's database. Maybe this will happen when the system gets going.
These MMS are sent to a phone number, and then picked out from the picture messaging web page. I used the iMacros product to see if it could be done simpler, but found that there was just not enough control. Th iMacros can click on a position on the screen, but prefers to activate the links inside the HTML.
The best that can be said for the method is that it works (at least until they change the web site again!)
The vi's to enter text into a web page and to click the mouse are included.
If I remember correctly, you can hook IE using active x to get click info. Might solve your positioning problem.
I'll see what I can dig up if your interested.
-
QUOTE (PaulG. @ Apr 27 2009, 05:44 PM)
You can always ignore us (like 90% of the lurkers
 ). Or you could read it during work time when your paid for it...lol.
). Or you could read it during work time when your paid for it...lol.QUOTE (jdunham @ Apr 27 2009, 04:09 PM)
Queues are cool that they can even the load if your data is bursty, but queue or no queue, if you're not processing fast enough, you have a problem that queues couldn't fix.Unfortunately my data isn't "bursty". It is multiple continous streams with control on top. No problems either.
QUOTE (jdunham @ Apr 27 2009, 04:09 PM)
If I were to adopt the same strategy in the current project I would end up with 87 queues

QUOTE (jdunham @ Apr 27 2009, 04:09 PM)
OK, I give up trying to convince you. We obviously use queues in very different ways. I find them useful, even indispensable. My team's code doesn't suffer from any of those things you say queues suffer from, and we're doing things that you say are nearly impossible in LabVIEW, and they were pretty easy to code up and have great performance and scalability.Ummm. Are you referring to spawning multiple (200+) threads like in the BT client? I don't think that is possible. Especially if you can only have cores x 4 threads.
QUOTE (jdunham @ Apr 27 2009, 04:09 PM)
It's fine if you don't want to use more queues, but I don't think you'll manage to dissuade the rest of us.So I guess your in the Q or die camp
 (but suspected that quite a few posts ago)
(but suspected that quite a few posts ago) -
-
QUOTE (jdunham @ Apr 27 2009, 09:41 AM)
QUOTE (jdunham @ Apr 27 2009, 09:41 AM)
Why do you need wait functions if there is data available?Because you may be busy doing something else that is time critical and higher priority.
QUOTE (jdunham @ Apr 27 2009, 09:41 AM)
So many why's. I've already explained that one.
QUOTE (jdunham @ Apr 27 2009, 09:41 AM)
Why would you let a queue consumer get data that wasn't meant for it? That's what I call a bug.How can you not? Since there is data in the queue how does it know that its not for it? Thats what I call the nature of queues.
QUOTE (jdunham @ Apr 27 2009, 09:41 AM)
Don't get all Trekky on me now
 And I know why as queue is useful, in the same way I know that a car is useful unless you in a swamp.
And I know why as queue is useful, in the same way I know that a car is useful unless you in a swamp.QUOTE (jdunham @ Apr 27 2009, 09:41 AM)
Well, do a Google search on "Global variables are bad". I got 400,000 hits. They are considered dangerous in every language. I have been using more unnamed queues and notifiers lately so that they are not available globally.Do a search on "kill Bush" and you get 12,700,000. Your point is?
This is what NI have to say on it:
http://zone.ni.com/devzone/cda/tut/p/id/5317
QUOTE (jdunham @ Apr 27 2009, 09:41 AM)
About my version of the sample application, I tried to add some asynchronous behavior to show the power of the queues. Did you read all the diagram comments? I though that would have answered your questions. It would be easy to modify it to match the original more closely. I took all the globals out because I think they are a defect, not a feature.For asynchronous behaviour they are already in while loops. If data is lost, then I'm not really sure what you were trying to demonstrate with the example.
-
QUOTE (jdunham @ Apr 26 2009, 06:29 PM)
QUOTE (jdunham @ Apr 26 2009, 06:29 PM)
Same thing would work better with a notifier. No polling, no latency.Oooooh. No. Because then the UI would have to wait on the notifier(s). Also if you go down this path you end up with notifiers everywhere like a plague of mosquitos. A pain in proverbial to debug. All I have to do to debug is watch the global. There is no need for sequencing so a notifier is not useful.
QUOTE (jdunham @ Apr 26 2009, 06:29 PM)

QUOTE (jdunham @ Apr 26 2009, 06:29 PM)
Amen, brother. Dataflow is your friend. Easy to read, simple coding. But when you have parallel processes, dataflow doesn't apply. If they need to share data, you can use globals, which have lots of problems, or queues, which don't.The only problem with globals arises when you require synchronisation. But that isn't really a problem, it is (a very useful) feature of globals. The fact that it creates copies of data is a drawback (if you were running on a ZX spectrum...lol). But a queue isn't a replacement for globals as you point out in your example (removed the stop button from the user). And even in the first example it was used.
QUOTE (jdunham @ Apr 26 2009, 06:29 PM)
QUOTE (jdunham @ Apr 26 2009, 06:29 PM)
I generally run these handlers with infinite timeout, so there is no timeout case (and no wait function). LabVIEW's internal execution scheduler may have to poll the queue somewhere deep in the bowels ofLV, but that's not exposed to me. We have dozens of queues waiting in parallel with very low overhead and very low latency when an event is fired, so I suspect it's not polling at all, but is really sleeping. I don't know what you mean about a difference between queues and notifiers. As far as waiting and timing out, they act exactly the same.Queues do not have a wait function. Yes you can get similar behaviour IF you only ever have 1 message on the queue at asny one time, but if your producer(s) is faster than your consumer this is rarely the case. Therefore having an indefinite timeout makes no difference as your sub process still needs to inspoect the message to see if it was meant for it. So it is not sleeping, it is inspecting. You would then need a case for if the message wasn't for it and you can't just let it run through a tight loop so a wait so many milliseconds would be needed. So it's not sleeping evertime there is a message on the queue regardless of who it is for.
QUOTE (jdunham @ Apr 26 2009, 06:29 PM)
Ummm. It doesn't do what it says on the tin.
It uses no globals, because you have removed the "Stop" from the user in SubVI1. The original example uses a global also.
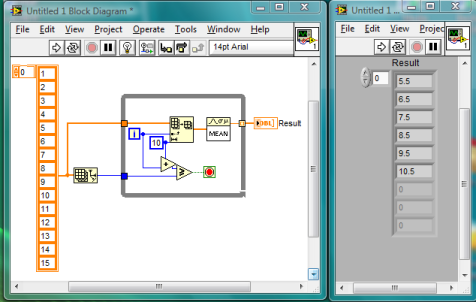
In the example I posted (ver 2), I set the aquisition time to 0ms and could acheive 3 ms of aquisition (mainly due to the 1ms delay I have in my notifier VI). All of the VI's show 3ms and all the vi's show the same loop iteration thus proving they are all capturing the aquisition "Event" with no loss.(well. The aquisition VI might show one more since it gets an extra go after you press stop on the aquisition vi).
In yours, however. If I set it to 0ms the aquisition vi runs like the clappers (6229 for the length that I ran it) but the others show significantly less (2654). What is happening to the other 2654 samples of data?
-
QUOTE (Aristos Queue @ Apr 26 2009, 08:50 PM)
Let me assure you -- it really does go to sleep. There is no CPU load at all from a sleeping queue prim. There is no polling for data. Thread A executes and goes to sleep on a queue. Thread B runs free. When Thread B puts data into the queue, it wakes up thread A. In fact, it doesn't even put the data into the queue. It puts it directly into the output of Thread A and A wakes up and starts running as if it had just gotten the data out of the queue.Shorter ones first...lol.
Even if there IS data in the queue but not for that "thread"?
And (just a point to fill my knowledge gap) Are you saying that 2 while loops (or 50 even) will run in their own separate threads?
-
QUOTE (jdunham @ Apr 25 2009, 08:12 PM)
I'm not exactly sure what you mean. I think the event structure is queued. If you invoke two or more value(signalling) properties then they will be handled on a FIFO basis, since there is some kind of queue behind the event structure. I agree it would be cool if LabVIEW made it easier to handle user and programmatic events in the same structure. I know you can register your own event, but it seems like a pain to me, when the queues are so easy.QUOTE (jdunham @ Apr 25 2009, 08:12 PM)
they use queues to communicate with the various processes they need to effect. Often the receive status updates via notifier.I tend (generally) to use one or the other as in many cases as (you point out later) their features can be seen to be synonymous.
QUOTE (jdunham @ Apr 25 2009, 08:12 PM)
Generally it boils down to an error indication, start, stop and pause.
Lets assume the system is monolithic and only runs on one machine (a test/inspection machine for example) and say I have 32 digital inputs that indicate alarm conditions on of which only 8 of them are to be displayed on the user interface. I can (and do) arrange with the electrical guys that those 8 are all on the same port (I give them a spreadsheet with the pin numbers of the DIO device and define which sensors/outputs will be attached to what).Now I can have an asynchronously running digital input VI that all it has to do all day is read the status of those digital inputs and write them to a global as a 32bit number. Then I can easily mask them off in the user interface just by polling that global and (with the number to boolean function) show the user which ones they are in a 1D array of booleans or I can use the number as an index into an array of strings to show an error string. If you have multiple banks (like 128 in banks of 8) you can partition those banks for each hardware subsystem). Then your on-screen alarms become a 2D array of booleans, each row (or column) associated with each piece of hardware. Any other VI can also read that global if and when it wants to (none of that critcal section rubbish with Labview
 ). So if some other part of the system needs to now about it it can. Quick, simple and as I said takes a few minutes.
). So if some other part of the system needs to now about it it can. Quick, simple and as I said takes a few minutes.Now. Distributed IO is a different kettle of fish!
QUOTE (jdunham @ Apr 25 2009, 08:12 PM)
Well I found it difficult to manage an event-driven user interface in the same loop as several acquisition/control processes. If some of those processes had to maintain an internal state, it got even harder. If I wanted to reuse those hardware items in other applications, it was often easier to just rewrite the code. With a queue handling the inputs for a given device, I can have a modular program for that device which maintains any necessary state and accepts asynchronous event messages.I have always had the UI in its own loop. I used to "break" the link with globals and dynamic loading (the example I posted would have used globals instead of notifiers and would have been quite messy), now we have other tools like events, notifiers, queues, semaphores and the like. We have the tools to make more elegant solutions.
QUOTE (jdunham @ Apr 25 2009, 08:12 PM)
QUOTE (jdunham @ Apr 25 2009, 08:12 PM)
I am certainly open to other opinions. What architecture do you use for your majority of large applications where queues were not the best solution? Do you handle user input and environmental input (alarms, triggers, other state changes) in the same loop of execution? Do you pass messages between with some other mechanism? Do you run a monster event loop, and run everything in the timeout case, and make sure that every subvi can finish in 50ms or so? I would love to hear more about other architectures you prefer.See above
QUOTE (jdunham @ Apr 25 2009, 08:12 PM)
QUOTE (jdunham @ Apr 25 2009, 08:12 PM)
My current project has about 4000 VIs, and probably 2500 are running at in the main app, with about 25 parallel static loops and 2 to 100 or more dynamically spawned loops, all of them containing at least one queue or notifier for message passing and synchronization. When this system grew to about 1500 VIs, we couldn't maintain the code any more until we refactored everything and used a lot more queues. I think that a much smaller app of only a few dozen VIs could still benefit from using queues if there are mulitple asynchronous tasks.That depends on how much info they need to do their job. I prefer autonomous encapsulation of the task as it makes the code a lot more understandable and intuitive (and less documentation
 )
)QUOTE (jdunham @ Apr 25 2009, 08:12 PM)
QUOTE (jdunham @ Apr 25 2009, 08:12 PM)
Well I have a couple comments here. For one, I'm not a huge fan of over-using state machines. I always prefer dataflow. If I have to do four operations, I'd rather see four subvis in a row than four cases in a state machine loop. But other people really like them. The large app I mentioned above has very few state machines.Ditto. They hide functionality, can be difficult to conceptualise and break dataflow. That said. They do have the advantage that they compact code and enable selective branching. If used spareingly a definite asset. But often abused. I think were on the same page there

QUOTE (jdunham @ Apr 25 2009, 08:12 PM)
QUOTE (jdunham @ Apr 25 2009, 08:12 PM)
Your example is a better solution to that problem, but we already established that the author wasn't trying to solve a problem so much as illustrate a scalable architecture.Better? No. They both fulfill the spec. I think one is easier to read and understand because it uses Labviews dataflow more and the other is more complex and difficult to read because it breaks that dataflow and adds complexity to compensate.
QUOTE (jdunham @ Apr 25 2009, 08:12 PM)
QUOTE (jdunham @ Apr 25 2009, 08:12 PM)
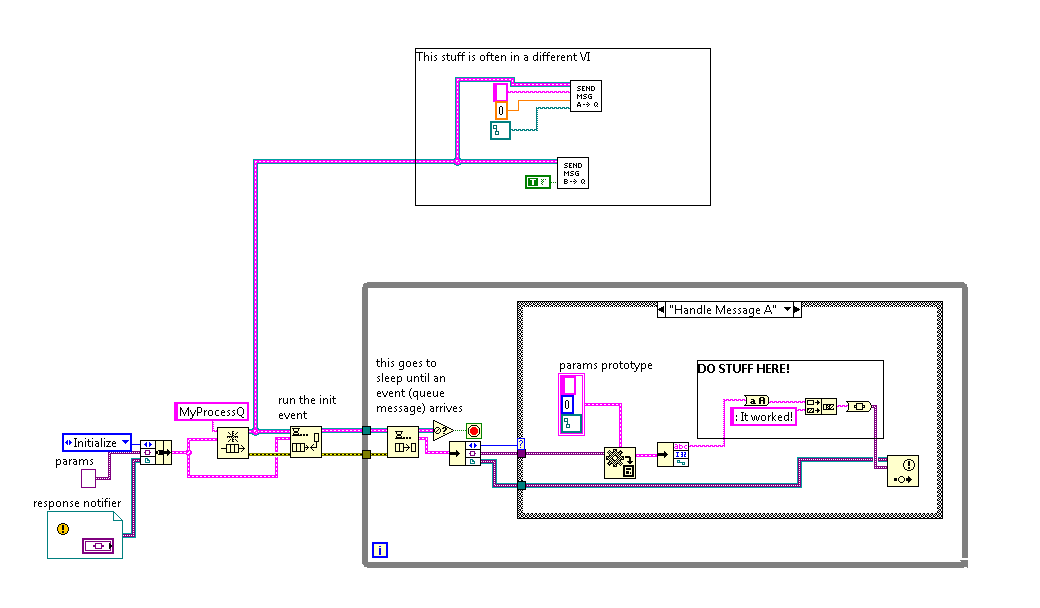
I made a VI, which isn't too much different than other stuff you've seen but I'll post it anyway. It's an architecture that is working well for me. I would still love to see more about what is working for you in your large applications.Many thanks.One observation. It doesn't "go to sleep" it polls the status until it has something in the queue. So I'm guessing you have a wait so many milliseconds in the timeout case. That is the big difference between queues and notifiers. If you add another notifier (wait) to my example before the acquisition another after the AQ notify in the Subvi 2 (notify) and a third before the while loop in the main (also a notify just to kick off the aquisition in the first place) then you can run the system fully synchronised, flat out with no loss of data (3ms). You can't do that with a queue.
See attached:
Download File:post-15232-1240703966.zip
And if you read all that your a star....lol.



Hello together
in LAVA Lounge
Posted
Welcom Markus.
Not sure about a good time, but is always interesting