-
Posts
5,004 -
Joined
-
Days Won
311
Content Type
Profiles
Forums
Downloads
Gallery
Everything posted by ShaunR
-
Is your VI shared, re-entrant?
-

Waveform Graph digital display intermittently drops to zero
ShaunR replied to Daryl's topic in User Interface
Yup. I can see this too with your example (@200ms). Tried it in LV2009, 2014 & 2015 and they all exhibit the behaviour. Looks like a Graph Indicator bug since the using a "Convert From Dynamic Data" set to "scaler" and placing an indicator doesn't do it. -
Has no-one created a vmware image yet? Building Linux distros is like unraveling a jumper with chopsticks to make a tank-top.
-
This was a problem for me too.cThere is no elegant solution that I know of. You either architect your software to call dynamically the functions you need (plugin architecture) which works great in classic Labview where nothing is broken but you are stuffed if you use classes. Then, as you describe, the conditional disable. This is the only alternative I have found so far (open to more ideas) that works for everything but has some caveats (like the dependency has to be installed first so upgrades are difficult). I just put the onus on the developer/user to add a conditional disable tag into their project which also has the side effect of allowing them to choose whether to ship with that feature or not if they do have it (toolkits, obviously). The default shipped state is the plugin is disabled and they add the tag when they enable it which will either activate the feature if it is installed or break their VIs.
-
Nice. We didn't need a spec, but since you've given us one - polymorphic VIs are great. They never encapsulated Moveblock. I don't know why - it's the single most useful function for CLFNs. Tempting to wish for callback features but I'm ambivalent. If there is one good way to crash a LabVIEW program, it is to write some of it in another language. CLFNs are a last resort when no other options exists rather than standard coding practice. After all. If you want to write GPF ridden software, there are better languages like C and C++
- 8 replies
-
- c compiler
- ansi c
-
(and 3 more)
Tagged with:
-
OK. So it is a thin wrapper around the Tiny C Compiler.(Note that TCC is LGPL licenced ) It looks like the "State" is an opaque pointer to a structure so you might want to choose "Unsigned Pointer-Sized Integer" so that it is 32 and 64 bit ready. I would also suggest putting each function in a case structure and checking for 0. You can't test a pointer in C to see if it exists so the best you can do is hope that the library returns null pointers when memory is released or memory can't be allocated. For your DSNewPtr, which is a LabVIEW function; there are already VIs for that and others. I forget whether they are under resources or in vi.lib but I think you should separate out LabVIEW functions and application specific functions. LabVIEW functions are reuseable and usually cross platform , whereas application specific ones are or may not be. Looking forward to being able to auto-compile libbitcoin from LabVIEW
- 8 replies
-
- 2
-

-
- c compiler
- ansi c
-
(and 3 more)
Tagged with:
-
Amen! Although I don't think I've seen it. It was more to poke fun at eulogising ones own software.
-
Software is like a fart. Yours is OK but everyone elses stinks.
-
Been there, done that. T-shirts on sale soon. That's something I've been meaning to get into. I've got a little project for stripping out requirements and turning them into code that I think would benefit hugely from a neural net for natural language parsing.
-
Sweet. Looks like some nice little projects there. I too have a shedload of 1/2 finished projects. It took me, probably 10 years before I published one of them. I productionised a couple and gave a few away as freeware (you'll see them on my site an on here in the CR) and still I have about 30 that I use but have never published. That last 10% is 50% of the work Your ASCII art one looks interesting. I've been looking at visualising encryption keys and SSH has an ASCII art one so I'd like to play with that a bit. OTF compiler for encryption? Please! That's polymorphic virus country and you know it Looking forward to that one too Pure LabVIEW graphics sounds cool. The LabVIEW picture control, like most LabVIEW UI, is decades old so I'm looking forward to comparing with the Bitman library as well as the picture control. You might want to consider putting them in the CR so that versioning and updates are easier. Posting products in threads gets real messy, real quick and you always end up with support issues for outaded posts because they found them on search engines. You can put them in the uncertified to begin with then get them moved to the certified sections when you are happy with them.
-
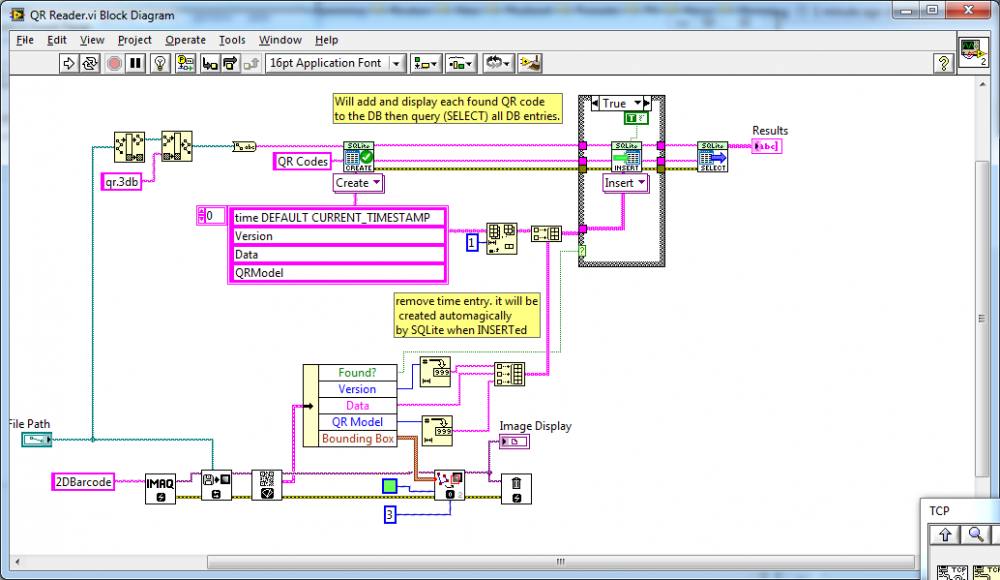
I took this QR Code example and modified it with the SQLite API for LabVIEW for a database to make a simple example. You will need to decide on the database you will want to use (SQLite, MSSQL,MYSQL, Access etc) but it demonstrates the how and the way forward. QR Reader.vi
- 1 reply
-
- 1
-

-
Off the top of my head....... I would probably do a find edges to locate the ordinates of the lines then draw the lines in the background colour (erasing them) then fill in the bits that were erased that went through the notes with a function like Fill Hole.
-
As a "real" LabVIEW programmer Maybe consider distribution via the LabVIEW Driver Network?
-
This is probably one of those situation where you ask 10 people and get 10 different answers. So here's mine. Open=Prepare resource. (General programming term used for comms (e.g. TCPIP) primitives, files, memory etc) OR Open=Particular function in LabVIEW to make a VIs front panel visible - only used in the FP context. Synonymous with "Show". Called/call = execute. Load/Loading/Loaded=Open (prepare resource meaning) from disk and place into memory... Launch=Run When Opened=Open (prepare resource meaning) then show the front panel (we can argue about this step) then execute.
-
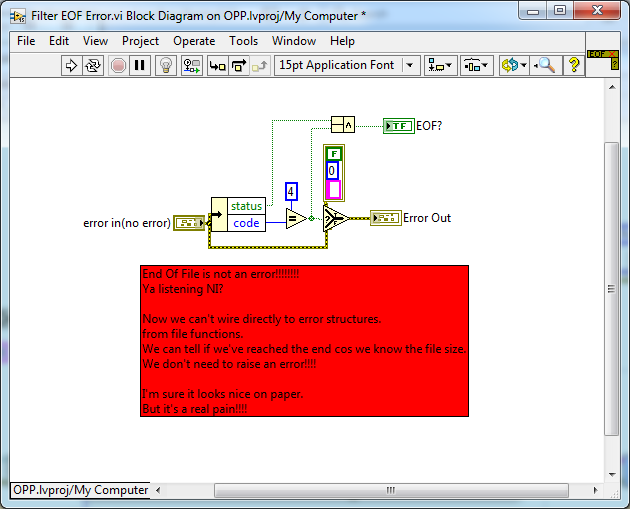
Well. To be fair. The originals didn't have error clusters; just a boolean for when EOF was reached. But you could have (and am glad you didn't) normalised the behaviour with the Read from Text File function which is an enormous pain.
-
Ooooh. Now I want to know if speedy has the overflow or fixed behaviour
-
Aha. You've deprecated it to a warning. You are a legend Now please walk over, and smack with a wet sock, whoever is responsible for "Read From Text File" For posterity! (circa 2009)
-
Sure it is. Save and load it as a string and you can have any format you like. There is no date/time "type" in JSON!. Serializing dates to and from LabVIEW in a cross boundary way is, at best, a kludge and you always have edge cases (different separators, different offsets, different epochs.- the list goes on). If you view the date/time JSON object as a "helper" that tries the common types but specific ones you should just convert manually then there will be less bloat of the function as it trial and errors umpteen different formats and takes 10 hours to do so. You could even save the time and the format string along side it so you know how to re-interpret it. This cat has many skins. I never offer a date/time conversion in any toolkit for these reasons, but if I did, it would be a default conversion format with a string input to override with a custom one. That's my view, anyway.
-
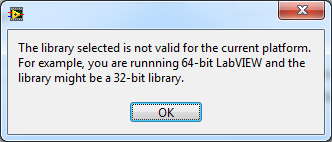
If it were a bitness problem then you would see this error. You can also run the software without a broken run arrow to get a result. There seems to be little wrong with the LabVIEW end of things - you should be asking the supplier whats wrong with their DLL or looking at configuration of their system/device.
-
Do they throw an error 4 when they read the entire file? (one of my pet peeves)
-
If it's good enough for Apple, Google and now Microsoft ..........
-
If the user makes a mistake it is an error (on the users part). If it he needs to interpret a 20 GB log file to guess why, then that's an uncaught error with no recovery (on the programmers part). I always say, errors are for programmers only because users just want software that works-preferably with one button "Start". As a user of your software I do''t want to be "trained" how to interpret your logs of gibberish or wade through reams of irrelevance to find out what to wiggle. I want to know whats wrong and what to wiggle so it works. Well. Changing a background colour doesn't require pre-defined controls on the front panel and is supported by all controls/indicators. I'm not sure how you used an image but I would imagine it needed an image control next to each unless it was a list/tree or something. You can get (and save) lists of the controls and limits (from your database ) and have a generic check/set that just iterates over the visible controls and sets the colour and limits. This enables you to also tell the user why the value they entered is incorrect if it's outside limits and what is acceptable to enter. See the "Panel Settings Example" to see how this might work. The cluster? For me, no. That's used also for sequencing.
-
Without getting into error strategies; I haven't used the default LabVIEW handler in real applications since, probably, version 7. Yes I do use it for examples and quick checks of the error wire for debugging but I want a dialogue that is uniform with the rest of the look of the application for real apps. So I have a customisable 3 button dialogue that has images, on-the-fly translation, can query the database and has a timeout. It is used for errors, about boxes and confirmations - pretty much all dialogues - so the interface is consistent. I'm not a fan of the status bar for errors just as I'm not a fan of the status bar for mouse-over help. A one liner is not enough for users. They really need a plain [insert your language here] error message and an explanation of how to proceed. From a personal perspective, It just confuses me between something that's nice to know (which I associate with status bars so don't look often) and something I must know. For settings, I am a fan of the browser style of flagging errors. I.e change the background colour of the item and a message saying "sort that out!"
-

installation error LabVIEW 2014 64-bit on windows 10
ShaunR replied to kuroko's topic in LabVIEW General
Indeed. I think it makes sense for the other products since 32/64 "bit software" is the LabVIEW IDE bitness. So both 32 and 64 bit LabVIEW are supported.