-
Posts
5,001 -
Joined
-
Days Won
311
Content Type
Profiles
Forums
Downloads
Gallery
Everything posted by ShaunR
-

Help with using an analog video signal to process frames
ShaunR replied to cathair28's topic in Machine Vision and Imaging
Can't your PC box do it? You are plugging it in via USB, so making it available over TCPIP should be straight forward since it has Gigabit LAN and WiFi. Another alternative is Raspberry PI, but now we don't need your box or LabVIEW! -
A poor excuse. That is the kind of thing I would expect from a 10 yr old "script kiddie" over at the NI forums You are not, I suspect. (if you are, then we have lots of time to train you better )
-

Help with using an analog video signal to process frames
ShaunR replied to cathair28's topic in Machine Vision and Imaging
I think you are after an analogue frame grabber rather than a trans-coder.. Something more akin to the boxed version of the VRmagic AVC-2 (I've never used it, but give it as an example) -
Ssssshhh, Don't tell Rolf. But there is a superb library that no-one is supposed to use.
-

Real-time acquisition and plotting of large data
ShaunR replied to wohltemperiert's topic in LabVIEW General
Can you post the error? Row and column count return integers and should not have anything to do with decimal points. Yes. You can have parallel reads (but only a single write without getting busy errors) The syntax is standard SQLite SQL which is 99% compatible with M$ and MySQL. If you work with DBs, you have to learn SQL. -

Real-time acquisition and plotting of large data
ShaunR replied to wohltemperiert's topic in LabVIEW General
There is the "Data Logging" example which demonstrates this exactly in the SQLite API for LabVIEW. The issue would be whether you could log continuously at >200Hz - maybe with the right hardware and a bit of buffering. -
I sit firmly on the other side of the fence with things like this. When it's a choice between form over function; function wins - especially if the spec can be interpreted ambiguously via tortured semantics. Adhering to specs by observing a strict negative of a positive statement (it doesn't say they cannot be ordered, rather, I expect it was stated thus so it didn't restrict) is why the native 2013 JSON is inferior (IMHO) to this library - speed aside. This library works when the native one throws errors because the native one adheres even more strictly, word for word, to the spec. inf and NAN are examples of where some libraries have implemented function over form. In that case, it was in spite of the spec which specifically disallowed it. There is precedence here if there is enough benefit. Would it really hurt that much to make the output look exactly like the input which is what we all kind of expect and know to be right? Relying on a specs throw away description about an unordered list seems a bit of a cop out to me and it would probably make testing much easier and simpler as you could do a straight input/output compare. It wouldn't break existing code, either. So I'm not sure what the resistance is apart from the effort required which has already been done.
-

REx - Remote Export Framework and Remote Events
ShaunR replied to Norm Kirchner's topic in Application Design & Architecture
Hmmm. I just sat down and attempted to give Rex websocket capabilities since it is already event driven, follows the Open. Write/Read and Close structure and *should* have slotted straight in with a simple wrapper (I'm updating the Websocket API to use HTTPS and thought this would be a great use case). The only issue I found was that there is no background "service", so to speak, that could monitor the TCPIP to generate the events since VI Server methods evoke directly remotely (via the ACBR). Did you add a background VI service, or did you go through the web service interface to get to the users webservice VIs?- 34 replies
-
Once the buffer has every point written to, continue writing at buffer[usersize+1] wrapping back around to buffer[0] after buffer[usersize+usersize] is written Nearly.. After i=usersize, you wrap around to buffer[0] all the while writing to buffer and buffer[i+usersize]. Then, if you read at index i for a length usersize, you will get what you need.
-
It doesn't prevent wrap-around from happening. It means that you can read a contiguous array of data at any point in the buffer without having to chop and concatenate.
-
Not so trivial in native labview since to read contiguous bytes using the array subset, you need to split and wrap the array by making copies and sewing them together again. You'll be lucky of it doesn't get a lot slower than a rotate. There is one that uses direct calls to the LV memory manager though, but a rotate is much easier.
-
No and you can't (nor should you want to) LabVIEW Threading Model. For a detailed technical description see section 9.7 of this document
-
I would suggest you look into SQLite.There are a couple of LabVIEW libraries for it and you will be able to query the remote database and update your local (on-disk) one and pretty much run the same queries on it as you would do remotely. Really, though. It is an infrastructure problem, not a programming one. Your IT department should be offering you solutions rather than passing the buck.
-
I think event refnums are fairly well documented and there was a good presentation by Jack that demonstrated the issues. What is not clear and unintuitive is what happens if you place two event structures and connect them to the same FP control. This is THE rookie mistake, after all, I just wanna add another function to operate in parallel when I press that button, right?
-

How to keep track of multiple UI control references
ShaunR replied to doradorachan's topic in User Interface
Now you know how to make all your string controls/indicators URL aware without faffing around with xControls or cluttering up yer main diagram- 4 replies
-
- control references
- ui references
-
(and 1 more)
Tagged with:
-

How to keep track of multiple UI control references
ShaunR replied to doradorachan's topic in User Interface
- 4 replies
-
- 6
-

-
- control references
- ui references
-
(and 1 more)
Tagged with:
-
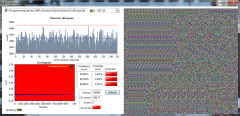
From the album: ShaunR
SQLite database statistical analysis with AES 256 CBC encryption. N.B. 1. Multiple encoding runs produce new database byte-map. - differential analysis resistant. 2. Statistically indistinguishable from random data. - statistical analysis resistant. -
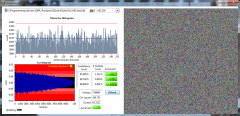
From the album: ShaunR
SQLite database statistical analysis with AES 128 ECB encryption. N.B. 1. Multiple encoding runs produce identical database byte-map - susceptible to differential analysis. 2. Information leakage and correlation especially for zero values - susceptible to statistical analysis.. -
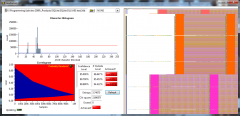
From the album: ShaunR
SQLite database statistical analysis without encryption-
- none
- encryption
-
(and 1 more)
Tagged with:
-
Unwrap Phase VI
-

I can't be the first one to have tried this. XD
ShaunR replied to Sparkette's topic in LabVIEW General
I expect you are. When you program for machines and instruments from the real world. Edge cases of the programming tool are pretty dull -
Not quite since you can only build one "Top Level Vi" according to the Application Builder (so it's not a "hint") and "sub VI" has a definite dependency hierarchy (only appears in the hierarchy window if tied by the diagram) - pedantry prevails! 1. All VIs have front panels and diagrams at design time. 2. What does "Top Level" mean? (top level of application? top level of a hierarchy of other VIs? Top level of a notional design partition?) 3. If one VI calls another VI dynamically then exits, is that called VI a sub vi of the caller that has now exited? Currently, the only unambiguous parlance is that if a VI has another VI on it's diagram, then the VI on the diagram is a sub vi of the VIs diagram. I'm suggesting that if you define "Top Level VI" as being the pinnacle of a stack of VIs tied by its diagram, then everything fits nicely and you don't need all the other nomenclature. You just need to rename what the application builder calls the application entry point (which is currently Top Level VI) and that removes all ambiguity and AQ can name his "Not-Top-Level-Vi" as a "Top Level Vi". That IS simple and can be explained with the VI hierarchy window to the confused.
-

Possible to dedicate an entire CPU core to software timing?
ShaunR replied to Sparkette's topic in LabVIEW General
I think you are thinking of the myRIO. The myDAQ is A/D IO only and what they used to call Elvis. -

Possible to dedicate an entire CPU core to software timing?
ShaunR replied to Sparkette's topic in LabVIEW General
I believe you can create a counter using the DIO on a MyDaq. If you are doing it as a technical exercise - fine. If it is for a real project then I would just get a USB to serial cable and be done with it