-
Posts
4,998 -
Joined
-
Days Won
311
Content Type
Profiles
Forums
Downloads
Gallery
Everything posted by ShaunR
-

Optimization of reshape 1d array to 4 2d arrays function
ShaunR replied to Bruniii's topic in LabVIEW General
Nope. I can't beat it. To get better performance i expect you would probably have to use different hardware (FPGA or GPU). Self auto-incrementing arrays in LabVIEW are extremely efficient and I've come across the situation previously where decimate is usually about 4 times slower. Your particular requirement requires deleting a subsection at the beginning and end of each acquisition so most optimisations aren't available. Just be aware that you have a fixed number of channels and hope the HW guys don't add more or make a cheaper version with only 2. -

Optimization of reshape 1d array to 4 2d arrays function
ShaunR replied to Bruniii's topic in LabVIEW General
Post the VI's rather than snippets (snippets don't work on Lavag.org) along with example data. It's also helpful if you have standard benchmarks that we can plug our implementation into (sequence structure with frames and getmillisecs) so we can compare and contrast. e.g -

OpenG LabVIEW Zip 5.0.0-1 - stuck at the readme
ShaunR replied to PA-Paul's topic in OpenG General Discussions
This is why it takes me hours to make an ECL build that works and is one of the many reasons only Windows is now supported (can load from same dir). Even then. I have to fight VIPM to get things in the right places. I refuse to do #2. -
Well. There's a few problems but the reason it's not showing the next image is because you increment the counter during acquisition until it's 300 and when you start the next acquisition it indexes into the path array at 300 (which yields Not A Path). You've confused your 30 second timer with the file index. Make a proper timer with a time function and increment the index on stop.
-

Parallel For Loop versus Async Call and Collect
ShaunR replied to Stagg54's topic in LabVIEW General
Yes but you'd need to define "reliably". I think there would be few milliseconds of jitter and probably a minimum of about 4ms. -

Parallel For Loop versus Async Call and Collect
ShaunR replied to Stagg54's topic in LabVIEW General
There are surprising few situations where a parallel for loop (pLoop) is the solution. There are so many caveats and foot-shooting opportunities even if you ignore the caveats imposed by the IDE dialogue. For example. For the pLoop to operate as you would imagine, Vi's that are called must be reentrant (and preferably preallocated clones). If a called VI is not reentrant then the loop will wait until it finishes before calling it in another parallel loop (that's just how dataflow works). If a called VI is set to reentrant shared clones then you get the same problems as with any shared clone that has memory but multiplied by the number of loop iterations. Another that you often come across with shared, connectionless resources (say, raw sockets) is that you cannot guarantee the order that the underlying resource is accessed in. If it is, say, a byte stream then you would have to add extra information in order to reconstruct the stream which may or may not be possible. I have actual experience of this and it is why the ECL Ping functionality cannot be called in a pLoop. -

What is the best way to handle errors for external DLL/C code,
ShaunR replied to Neon_Light's topic in Calling External Code
I'm a simple programmer. Catch them all where possible (try { /* */ } catch (...)) and pass errors back as a return value. That's my tuppence. -
It's the example from MDI Toolkit for LabVIEW
- 54 replies
-
- alignement
- dialog
-
(and 3 more)
Tagged with:
-
If you put a Call By Reference Node in the case you've reinvented Dynamic Dispatch with extra steps.
-
Booh with bells on. Hello 7 hr build time.
-
Booooh!
-
- 54 replies
-
- alignement
- dialog
-
(and 3 more)
Tagged with:
-
They have fixed a bug, is my guess. Concatenating by using null char is a huge security smell. Multiple file types are [supposed to be] defined by using the semicolon separator. Does "*csv;*txt" not work?
-

Interfacing with digital x-ray plates?
ShaunR replied to grubin's topic in Machine Vision and Imaging
It's probably DICOM which is partially supported in the Biomedical Toolkit. -
The variant attribute cannot have duplicates. If you set it, it overwrites the previous values. With the "array with tag" you can have duplicates.
-

Convert to JSON string a string from "Byte Array to String"
ShaunR replied to Bruniii's topic in LabVIEW General
Try print(json.dumps(convert['test'], ensure_ascii=False)) -
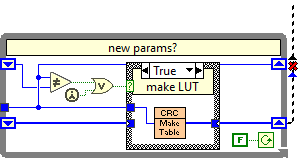
Yes. that's exactly what I am thinking (but poorly communicated). This is a common known gotcha for VI's with shift register memories (not the first call primitive per say). It will probably only bite you when you have multiple instances and where it's being used with different CRC types with different integer lengths. Here's an example: sub VI set to Preallocated (what we expect-11 more than the intialise value) sub VI set to Shared: If you run continuously, you will see other values as different threads become available at different times. rentrant clones.zip
-
Nice. This is probably one of the only times (1 in 1,000,000) I would suggest an xnode may be preferable-and specifically for the lookup tables which should always be more performant. With an xnode, one can pre-calculate the tables at design time based on the type and save the cost of generating the table at first run run. This will also mean that the calculation will be constant time whether first called or later. xnodes are tricky and complicated beasts so I could understand not wanting to go down this hairy rabbit hole littered with rusty nails. Speaking of the table generation; I noticed you have the VI set to reentrant clones. I think this will be a problem when you run multiple instances as the shift registers may not contain the values you expect per instance.
-
My takeaway from the roadmap is that they are concentrating on interoperability and relegating products to backend services. This was the direction NI were taking before Emerson but expect it's taken on a new impetus since the takeover. I expect the awful gRPC to be leading the charge so they can plug the NI products to their products. Unicode support isn't a consideration for that since the UI will be elsewhere.
-
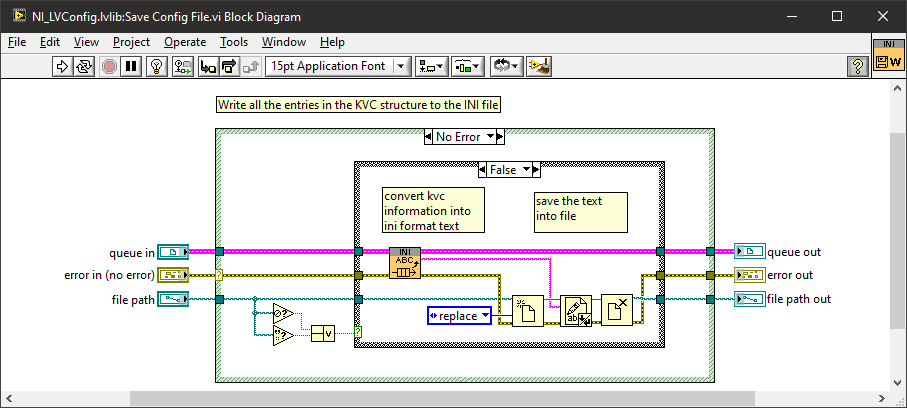
The ini (or config file as NI calls them) are only written when the reference is closed. You could put the flush in there but I don't think that's your problem. I have seen this before and it is usually on a failing hard drive or one that is about to fail. NTFS has a sort of self healing which is insidious for small files (less than the cluster size) and this is the usual result of it "healing". Larger corruptions are more detectable with chkdsk. (source) I would take a look at the S.M.A.R.T (Self-Monitoring, Analysis, and Reporting Technology) information of your disk and pay particular attention to the write failures/errors.
-

Listbox and MulticolumnListbox Border and Horizontal Lines Colors
ShaunR replied to dcoons's topic in User Interface
..and splitters. It's these sorts of issues that are the reason some of us abandoned the LabVIEW UI altogether. -

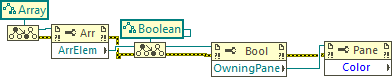
Get Boolean Image with Alpha - Get Array Element Background Color
ShaunR replied to hooovahh's topic in User Interface
There is an "Element" property for arrays. You can get that then cast it to the element type. Then your other methods should work (recursion). Boolean Get Image Testing_sr.vi -
To be fair. Those that VDB suggested aren't really protocols, they are middleware. One is based on OPC, the other is a translation service into an API. SILA is interesting in that it's basically what CoAPs does so I think your cartoon would definitely apply there Personally. I think they should just make all devices SCPI compliant and be done with it